
It’s been over three years since enterprises around the world had to pivot and transition to work-from-home setups. While some employees are still trickling back into the office, remote and hybrid work is not going anywhere.
This modern workforce has brought out an increasing reliance on cloud infrastructure, an essential tool for collaboration and business continuity. Technology like this isn’t without its risks though. In order to effectively mobilize a borderless workforce, it’s important to be aware of the cybersecurity risks reinvolved.
Cloud security is more essential than ever
Cloud services used to be a “good to have” competitive edge, but now it has become an integral business enabler. According to an IDG report for 2022 Cloud Computing research, 69% of organizations have accelerated their cloud migrations over the past 12 months and cloud budgets continue to increase – on average, organizations will spend $78 million on cloud computing over the next 12 months, which is up from $73M in 2020.
Aside from playing a huge role in disaster recovery and operational resiliency, cloud computing and infrastructure facilitates a free flow of information, making it easier for employees to access what they need and collaborate with others—even from their home office.
But this benefit is also its drawback. Information can easily be accessed by employees wherever they are, but the same is also true for cybercriminals looking to exploit vulnerabilities in the system.
With a broader attack surface on the cloud, there’s a pressing need for robust security controls and an increasing demand for technicians well-versed in the space. In fact, 19% of cybersecurity professionals in Canada consider cloud security an important technical skill or concept to learn. It can be the difference between mobilizing or jeopardizing the flexible workplace.
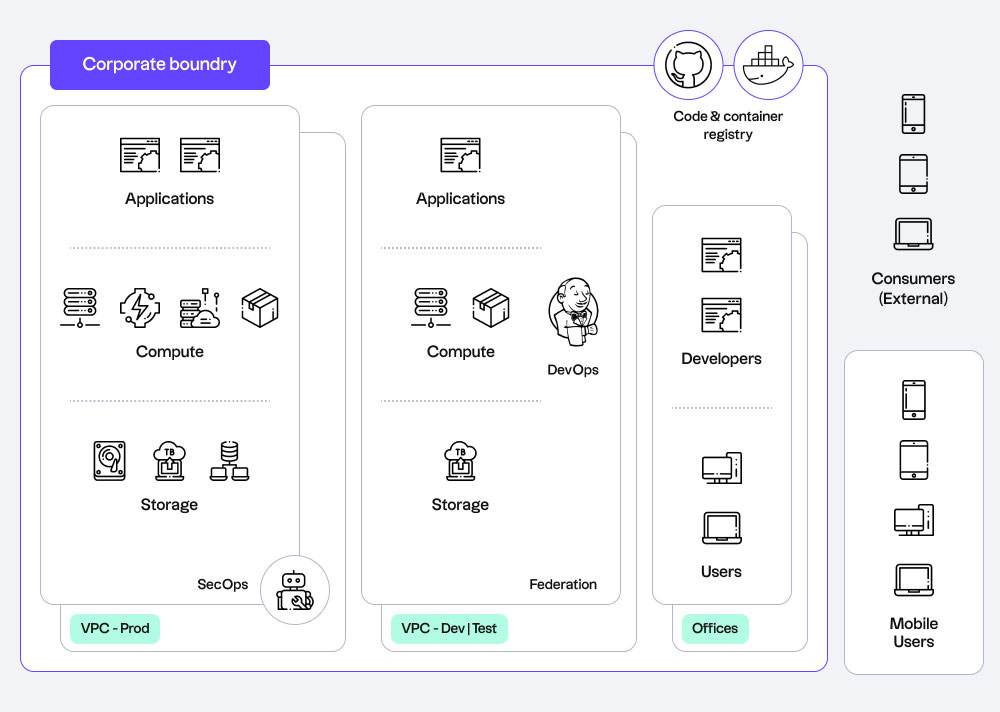
5 cybersecurity concerns in the remote work era—and how to address them
Security is one of the biggest barriers to taking full advantage of cloud resources. Without policies and controls to protect critical data, applications, and other assets in the cloud, organizations can face anything from financial loss to reputational damage.
According to a survey on IT and cybersecurity professionals, below are five significant risks posed by the remote work model.
1. Data leaking through remote endpoints
Organizations use the cloud for building data lakes and data-driven applications, housing massive amounts of customer, product, or organizational information.
With people working off premises, there may be a lot of remote endpoints being used to access these critical assets—from laptops to mobile phones. Any endpoint that’s unmanaged can be exploited to access sensitive data, install malware, or tamper core business applications.
To address authorization and authentication, implement Identity and Access Management policies to control and monitor who has access to critical organizational assets. Any access to the cloud should also have some form of Multi-Factor Authentication (MFA).
2. Users connecting through unmanaged devices or networks
Mitigating risk can be challenging for organizations with a BYOD (bring your own device) policy. Employees are connecting from their personal devices or their home networks that may or may not be secure, especially if they’re using older OS versions or legacy anti-malware solutions.
It becomes easier to attack corporate systems when edge environments are attached to unsecure devices or networks. There’s also a risk of theft; employees may lose their devices or have it stolen, leaving it compromised to potential cyberattacks.
To ensure both cloud and network security, regulate personal device use, secure VPNs, and deploy antivirus solutions that have central monitoring capabilities for remote devices. Consider encryption as well; encrypt sensitive information that is stored on, sent to, or sent from remote devices.
3. Adhering to regulatory requirements
While it may vary by country, regulations are in place to govern how sensitive data is being collected, used, and disclosed.
The goal is to protect critical assets and IT infrastructure, so compliance frameworks and audits must be part of any cybersecurity strategy. For example, in Canada, it’s important to remain compliant with the Personal Information Protection and Electronic Documents Act (PIPEDA).
To ensure compliance, it’s important to provide vigilant IT support where need. It’s also something to address when migrating to the cloud—any compliance functions existing on premise must be replicated on the cloud environment as well.
4. Access to core business apps
Employees working remotely often need constant access to core business applications, such as email and collaboration tools. These modern software applications, while convenient, are also vulnerable to potential cyberattacks.
For instance, there’s been a prevalence of digital fraud related to Covid-19, with email phishing scams being the most common. A lot of third-party software also allows easy access from personal devices, even if employees aren’t authorized to do so.
To decrease the risk of cyberattacks, make sure to secure communication channels and collaboration tools that employees regularly use. Educate employees by launching an awareness campaign on phishing and malware risks through email as well.
5. Lack of user activity visibility
A good cybersecurity strategy involves constant threat detection and monitoring, especially in infrastructure and systems that affect critical enterprise data.
With a distributed workforce however, there can be a proliferation of unmanaged personal and mobile devices accessing corporate IT environment and assets.
This partial or nonexistent visibility on relevant employee activity makes it difficult to monitor, audit, and address security risks and misconfigurations. This is why it’s important to set up and communicate any remote work security policies. Employees should be aware of the risks involved and measures to take.
Empower employees with cloud security
Ensuring security in the cloud should be a priority for any organization with a remote workforce, and this starts with mitigating the risks above. Enterprises should aim to strike a balance between convenience and security—empowering employees and protecting critical assets at the same time.
Cloud security strategies should address this and more, ensuring data encryption, implementing access control layers, and enabling proactive threat detection all while providing an optimal environment for the modern workforce.





